RIO DE JANEIRO, BRAZIL – Antivirus manufacturer Avast has published an alert for two attacks tampering with Internet router settings in Brazil. The change — made to at least 180,000 devices in the first half of 2019 alone — diverts access to certain sites to cloned pages, which then forwards any password entered to hackers.

Redirecting changes the destination of banking services and advertising material, as well as sending a cryptocurrency mining code to the victim’s browser.
The targets of the attack are domestic routers, such as those provided by operators and internet providers or acquired privately in the market to access the internet (see list of models below). The codes developed by hackers are placed on fake websites and use the simplified operation and factory passwords of these devices to replace the automatic configuration conveyed by the provider.
One of the active attacks, called “GhostDNS” or “Novelty”, was already known. The other, called “SonarDNS”, is new. According to Avast, the company’s products have picked up 180,000 tampered routers and blocked millions of attempted attacks.
Criminals insert the codes into fake pages. When the page is visited, the code attempts to change its setting through the browser itself, which may occur silently or through a fake on-screen warning of a “video player update”. No program is downloaded onto the computer to perform this attack: everything happens over the network and by “poisoning” the router.
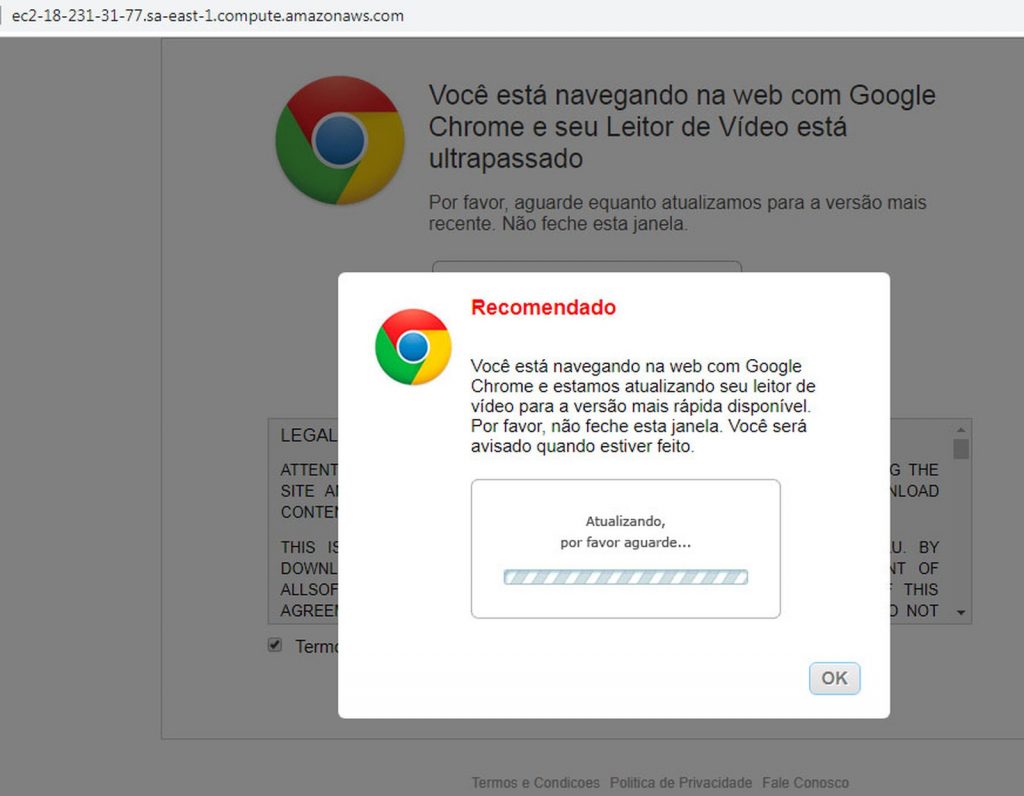
If the router modification is successful, Internet browsing will become dependent on a DNS (Domain Name System) service operated by criminals. The DNS is responsible for detecting the numbers (IP addresses) related to names, such as “www.riotimesonline.com”. The DNS used for internet access is typically provided by the contracted provider.
By gaining control over the victim’s DNS, hackers can provide fake IP addresses to searched addresses, leading the user to a cloned page designed by the criminals themselves instead of the correct destination.
Three in One
Hackers are redirecting access for three purposes: password theft, diversion of advertising, and insertion of a cryptocurrency mining code.
Password theft occurs when the victim enters the password on the cloned page, handing over the data to criminals. The diversion of ads replaces advertising material displayed on the internet, which can yield money for hackers.
Finally, cryptocurrency mining codes force the victim’s computer to work to achieve these digital currencies, consuming more electrical power and damaging notebook and mobile phone batteries. Attackers also make money from this, since participation in the cryptocurrency mining process entitles them to a share of the profits from the sale of these coins.
Thus, a single attack allows the criminal to profit in three different ways. Even if someone does not access banking services to fall victim to password theft, the hacker may still profit from the other two activities.
Attacked Equipment
According to Avast, the router models listed below are among those attacked:
- TP-Link TL-WR340G / WR1043ND
- D-Link DSL-2740R / DIR 905L
- A-Link WL54AP3 / WL54AP2
- Medialink MWN-WAPR300
- Motorola SBG6580
- Realtron
- GWR-120
- Secutech RiS-11 / RiS-22 / RiS-33
The following combinations of user and password are programmed in the code: user “admin”, passwords “admin”, “12345”, “123456”, “gvt12345”, “vivo12345”; user “root”, password “root” and user “super”, password “super”. All of the above are default or carrier-set passwords and must, therefore, be changed by the customer.

The steps to change the password vary depending on the device. It is recommended to refer to the product manual or the provider’s technical support for guidance. In some cases, it may be required to perform a “reset” (a special pushbutton on the unit that restores the default settings) to ensure that no hacker tampering has been retained in the device.
Avast also recommends updating the router’s “firmware” (embedded software) to the latest version. This procedure also varies depending on the model. Unlike App updates for cell phones or computers, these updates are not typically downloaded and installed automatically. The model-specific file must be downloaded from the manufacturer’s website and the update instructions must be strictly followed.
If in doubt, the free version of the Avast antivirus includes a feature named “Wi-Fi Inspector” that checks if the router has been tampered with.

